Security
Best Practices
A complete solution suite for enabling distributed remote working with Azure Virtual Desktop
Ebook
Implementation Guide
This guide provides Microsoft 365 administrators with best practices to secure their organization’s users, data, and infrastructure.
By implementing these recommendations, you can protect against common threats, ensure compliance, and maintain a robust security posture.
Comprehensive Best Practices Guide
Drawing from real-world experience, industry standards, and Microsoft’s own evolving security framework, this book offers a comprehensive roadmap for securing Microsoft 365 deployments of all sizes. This covers key areas such as identity and access management, data protection, threat detection, and compliance, while delving into advanced configurations and third-party integrations that can elevate your security posture.
Zero Trust Design
This covers key areas such as identity and access management, data protection, threat detection, and compliance, while delving into advanced configurations and third-party integrations that can elevate your security posture.

Expert
insights
An ongoing best practice article series on 365 Security Best Practices.
Read the Article Series.

Explaining the nuances of standard MFA versus Conditional Access, helping IT professionals and administrators make informed decisions to safeguard their Microsoft 365 tenants.
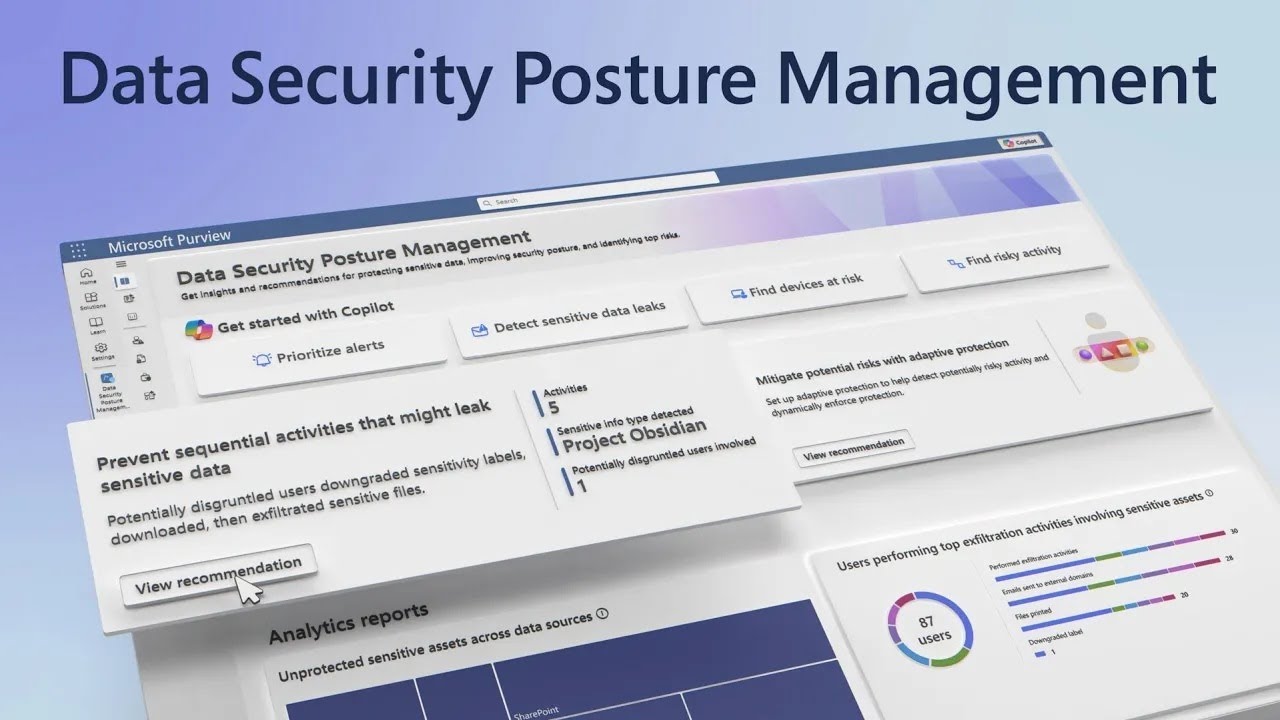
Microsoft Purview combines the former Azure Purview and Microsoft 365 compliance solutions into a single platform focused on data governance, protection, and risk mitigation.

How to secure guest sharing in Microsoft 365, offering expert strategies to balance collaboration with robust protection.
Solution Guide
The Solution Guide details adoption best practices and professional services from partners.

Architecture Design
Design and configure Identity Access, Firewall and VPN policies, and implement Intune for end point monitoring & protection services to ensure data security.

Implementation Plan
Design of the target Cloud environment, migration of legacy infrastructure, tailor your VDI images to the new environment and ongoing performance and cost optimization.


Download Solution Guide and browse Partner Services.
Directory
Listings of Partners who
specialize in 365 Security.
Key features include AI-powered advanced threat protection, automated email encryption, audit-proof email archiving, and unlimited backup and recovery for mailboxes, Teams, OneDrive, SharePoint, and more.
BlueVoyant’s Cyber Defense Platform (CDP) integrates internal, external, and third-party defense into a seamless, scalable solution.